This article is a part of a series of articles where I go through setting up RadSec (RADIUS over DTLS/TLS) between a Cisco device and Cisco ISE, using Microsoft's Active Directory Certificate Services to issue certificates to both the Cisco device (switch) and Cisco ISE.
You can find links to all of the articles in this series down below.
Cisco RadSec Part 1 - RADIUS over TLS/DTLS Overview
Cisco RadSec Part 2 - RadSec Certificate Template using Microsoft AD Certificate Services
Cisco RadSec Part 3 - Cisco Device Manual Certificate Enrollment
Cisco RadSec Part 4 - Cisco Device SCEP Certificate Enrollment
Cisco RadSec Part 5 - Cisco ISE RadSec Configuration
Cisco RadSec Part 6 - Cisco Device RadSec Configuration
Cisco RadSec Part 7 - Testing, Troubleshooting and Show Commands
Introduction
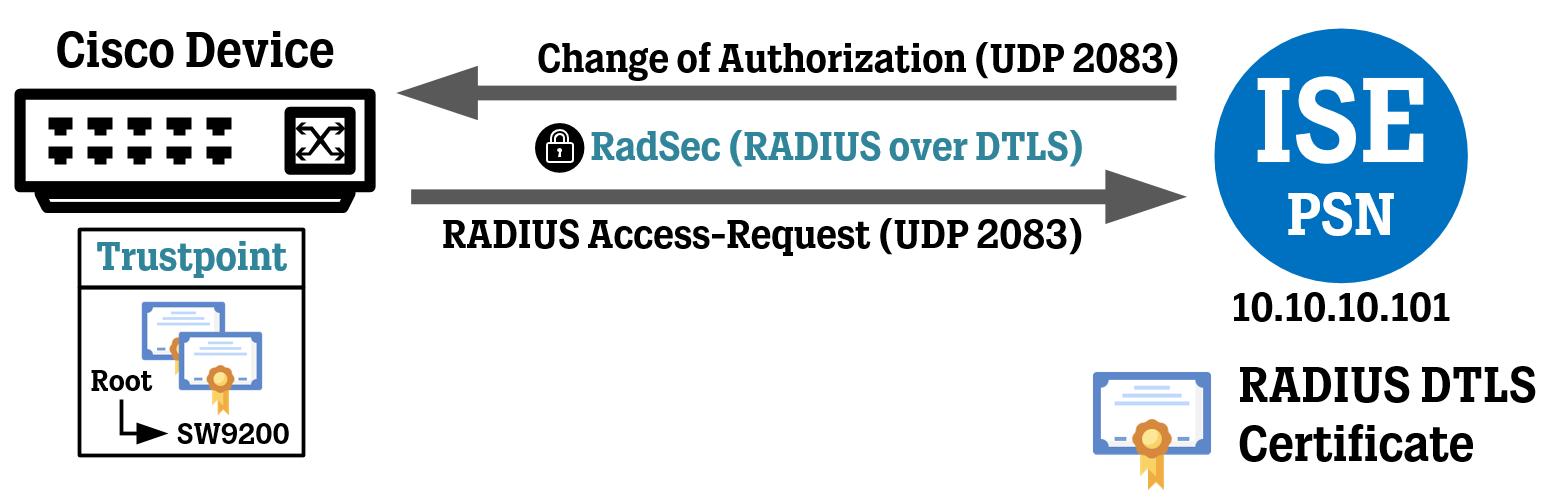
In this article, we will configure a Cisco device (a switch) to communicate using RadSec (RADIUS over DTLS) to Cisco ISE using certificates for mutual authentication between the two sides.
In this series of articles, the following hardware and software are being used.
Cisco Catalyst C9200L-48P-4X Switch running IOS-XE 17.3.5
Cisco ISE version 2.7
Microsoft Windows Server 2016
General RADIUS / AAA Configuration
If you have gone through the previous parts of this series of articles, everything is now in place for us to finally configure the Network Device, which is a Cisco switch in my case.
However, we will not be going through the complete configuration steps for AAA / RADIUS authentication on Cisco devices in this article, but if you’d like to get into the configuration on your own you can check out these two articles of mine that goes through IBNS 2.0 configuration template for IOS and IOS-XE to enable 802.1x / MAB authentication. These are configuration templates I use in my lab to test RADIUS authentication later on in this article.
SOLID CONFIG: Cisco IBNS 2.0 802.1x and MAB for IOS Switches
SOLID CONFIG: Cisco IBNS 2.0 802.1x and MAB for IOS-XE Switches
Replace the RADIUS server specific configuration in these two articles with the RadSec server configuration down below.
Cisco Device Configuration
If you have been following along since the first article in this series, then you know you had to make a choice between using manually enrolled certificate (Part 3) or SCEP issued certificate (Part 4).
For this article, we will assume that SCEP was used to issue the certificate to our Cisco device. If you are just copying and pasting the configuration from my articles, please note that the configuration in this article uses the SCEP variation of all references to the certificate Trustpoint (“TP-AD-PKI-SCEP”) in the switch.
If you did not use the SCEP method to issue certificate, make sure to adjust the configuration below accordingly so your configuration is not referencing a Trustpoint that does not exist!
The configuration below is pretty self-explanatory and we will only go through some of the details.
If you are trying to set up RadSec between a non-ISE RADIUS server using TLS instead of DTLS, most of the “dtls…” commands can simply be changed to “tls…” instead.
The “key” for RADIUS over DTLS should always be set to “radius/dtls”.
The “dtls match-server-identity hostname…” command specifies that the RADIUS DTLS certificate presented by ISE to the Network Device must have a CommonName (“CN”) or Subject Alternative Name (“SAN”) that matches or falls within what is configured on the Cisco device. Down below we will use the wildcard hostname “*.ksdlabb.local”, meaning the ISE certificate could have any hostname as long as it is within the domain ksdlabb.local like “ise01.ksdlabb.local”, or it could also be a SAN Wildcard certificate like the one we created in the previous article (where the CN is just “ise.ksdlabb.local” and the two SANs are “ise.ksdlabb.local” and the wildcard “*.ksdlabb.local”).
You can change the “dtls match-server-identity hostname…” command to “dtls match-server-identity ip-address…” to match an IP address instead of a hostname in the ISE RADIUS DTLS certificate, if you are not using proper DNS hostnames in your certificate naming scheme (for some very odd reason).
Since the certificates of both our Cisco device and ISE are issued from the same Root CA, the same Trustpoint is configured for the client and server configuration commands.
! Configure a RADIUS server with RadSec (RADIUS over DTLS) settings.
radius server ISE-PSN-RADSEC
address ipv4 10.10.10.101
automate-tester username SW-RAD-TEST probe-on
key radius/dtls
dtls connectiontimeout 10
dtls idletimeout 75
dtls retries 15
! Select VRF if neeeded
! dtls ip vrf forwarding MGMT
dtls ip radius source-interface vlan MGMT
dtls match-server-identity hostname *.ksdlabb.local
dtls port 2083
dtls trustpoint client TP-AD-PKI-SCEP
dtls trustpoint server TP-AD-PKI-SCEP
exit
! If you did not already have a RADIUS Test User configured, configure the one below.
username SW-RAD-TEST privilege 0 algorithm-type sha256 secret ciscodisco123!
username SW-RAD-TEST autocommand exit
! Put RADIUS server into Server Group.
aaa group server radius ISE-GROUP
server name ISE-PSN-RADSEC
deadtime 15
exit
! Enable Change of Authorization (CoA).
aaa server radius dynamic-author
client 10.10.10.101 dtls client-tp TP-AD-PKI-SCEP server-tp TP-AD-PKI-SCEP
! If you are using VRFs, use the command below instead of the command above:
! client 10.10.10.101 vrf MGMT dtls client-tp TP-AD-PKI-SCEP server-tp TP-AD-PKI-SCEP
dtls ip radius source-interface vlan VLAN
dtls port 2083
auth-type any
exit
With this configuration in place, we can now start testing and verifying that RadSec is being used to communicate between the Cisco device and ISE.
Next part: Cisco RadSec Part 7 - Testing, Troubleshooting and Show Commands