If you are looking to deploy IBNS 2.0 on Cisco IOS switches (not IOS-XE), please check out this article SOLID CONFIG: Cisco IBNS 2.0 802.1x and MAB Authentication for IOS Switches
This article is part of the “SOLID CONFIG” series, in which I cover some of the everyday configuration templates I have put together over the years to provide a solid configurational base for a specific feature, or use case.
Introduction
In this article, we take a look at a configuration template for deploying IBNS 2.0 802.1x and MAB authentication on Cisco IOS-XE switches, complete with global configuration such as Class maps, Policy Maps, and Interface configuration.
This configuration should work if you are deploying 802.1x / MAB on Cisco Catalyst 9200 / 9200L / 9300 / 9300L / 9400 switches running IOS-XE software.
What this configuration will do (in short)
Convert your AAA RADIUS authentication to “new-style”, which I recommend doing to make sure you use mostly the same configuration on both old and new switches.
802.1x authentication runs before MAB authentication (not concurrent).
Three 802.1x attempts before fallback to MAB (1 initial + 2 re-attempts).
Play around with these timers (dot1x timeout tx-period...) and the number of attempts (dot1x max-reauth-req...) to see what fits for you. Some use shorter timers with more attempts and some use longer timers with fewer attempts.
If for some reason 802.1x authentication is delayed from the client’s side and starts processing after MAB has been activated, terminate MAB and start the 802.1x process (matching the “agent found” condition).
If ISE is unreachable when re-authentication needs to take place, keep current authenticated sessions (ports) alive and pause re-authentication for those sessions.
If ISE is unreachable, activate Critical VLAN/ACL (via service templates CRITICAL_DATA_ACCESS and CRITICAL_VOICE_ACCESS) on ports that get connected AFTER the connection to ISE is lost. Tweak this to your needs, and have the switch select VLAN/ACL for limited or full access.
When ISE comes back online after being unreachable, clear sessions on ports that have the service templates CRITICAL_DATA_ACCESS and CRITICAL_VOICE_ACCESS activated on them (to trigger a proper authentication) and let normal ports with paused re-authentication (matching the “NOT_IN_CRITICAL_AUTH” condition) to resume re-authentication.
Activate IP Device Tracking to feed potential downloadable ACL (“dACL”) with source IP addresses.
Activate Device Sensor to collect data for device profiling.
No configuration for dealing with WebAuth on switches, let your guests use the guest wi-fi, in my opinion.
We will not be going through every command and what they do in this article, this is more of a “good to have” article with a configuration template you can use as a base for your own implementations of 802.1x/MAB authentication on Cisco switches.
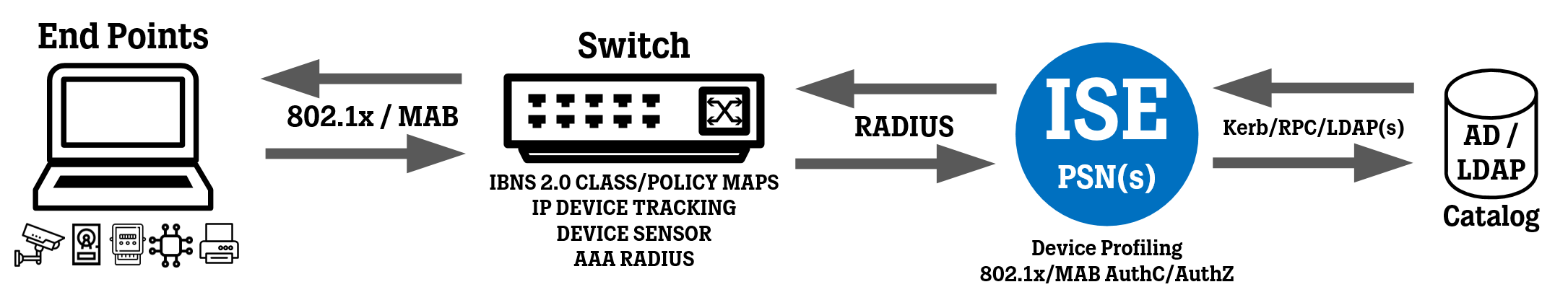
To refresh your memory on how a secure wired network is typically set up, please see the topology image below.
The following configuration has been tested on:
Cisco Catalyst C9200L-24P-4X running version 16.12.5.
Cisco Catalyst C9200L-48P-4X running version 17.3.4.
Commands that are highlighted below signifies values that might need to be tuned to your particular needs/organization, or named parameters to make it easier to read and understand the configuration for you, the administrator.
Global AAA Configuration
authentication convert-to new-style
yes
! Filter out 802.1x/MAB messages to keep logs clean, mostly useful after you have transitioned away from Open (Monitor) Mode.
! Create a logging filter ("discriminator"):
logging discriminator NO-DOT1X facility drops AUTHMGR|MAB|DOT1X|EPM
! Apply discriminator to switch local log buffer:
logging buffered discriminator NO-DOT1X informational
! Apply discriminator to a Syslog server:
logging host 10.20.20.101 discriminator NO-DOT1X
! Adjust timezone according to your needs:
clock timezone CET 1
clock summer-time CEST recurring last Sun Mar 2:00 last Sun Oct 3:00
service timestamps debug datetime msec localtime show-timezone
service timestamps log datetime msec localtime show-timezone
username SW-RAD-TEST privilege 0 algorithm-type sha256 secret ciscodisco123!
username SW-RAD-TEST autocommand exit
ip domain name yourCompany.com
aaa new-model
aaa session-id common
aaa authentication dot1x default group RAD-SERVERS
aaa authorization network default group RAD-SERVERS
aaa authorization auth-proxy default group RAD-SERVERS
aaa accounting update newinfo periodic 1440
aaa accounting identity default start-stop group RAD-SERVERS
aaa accounting network default start-stop group RAD-SERVERS
radius server RAD-ISE-PSN-1
address ipv4 10.10.10.101 auth-port 1812 acct-port 1813
automate-tester username SW-RAD-TEST probe-on
key ISEK3Y123!
timeout 2
retransmit 2
radius server RAD-ISE-PSN-2
address ipv4 10.10.10.102 auth-port 1812 acct-port 1813
automate-tester username SW-RAD-TEST probe-on
key ISEK3Y123!
timeout 2
retransmit 2
aaa group server radius RAD-SERVERS
server name RAD-ISE-PSN-1
server name RAD-ISE-PSN-2
deadtime 15
aaa server radius dynamic-author
client 10.10.10.101 server-key ISEK3Y123!
client 10.10.10.102 server-key ISEK3Y123!
auth-type any
radius-server vsa send authentication
radius-server vsa send accounting
radius-server attribute 6 on-for-login-auth
radius-server attribute 6 support-multiple
radius-server attribute 8 include-in-access-req
radius-server attribute 25 access-request include
radius-server attribute 31 mac format ietf upper-case
radius-server attribute 31 send nas-port-detail mac-only
radius-server dead-criteria time 5 tries 3
radius-server load-balance method least-outstanding
ip radius source-interface vlan MGMT
snmp-server trap-source vlan MGMT
snmp-server source-interface informs vlan MGMT
ntp source vlan MGMT
ntp server 10.10.10.1
dot1x system-auth-control
dot1x critical eapol
authentication critical recovery delay 2000
no access-session mac-move deny
access-session acl default passthrough
errdisable recovery cause all
errdisable recovery interval 30
Global IP Device Tracking and DHCP Snooping Configuration
ip dhcp snooping
no ip dhcp snooping information option
ip dhcp snooping vlan 1-4094
ip dhcp snooping database flash:dhcp-snooping-db.txt
device-tracking tracking auto-source
! Device Tracking Policy for Trunk Ports
device-tracking policy DISABLE-IP-TRACKING
tracking disable
trusted-port
device-role switch
! Device Tracking Policy for Access Ports
device-tracking policy IP-TRACKING
limit address-count 4
security-level glean
no protocol ndp
no protocol dhcp6
tracking enable reachable-lifetime 30
device classifier
! Enables Device Classifier, which is the local device classifier/profiler on the switch itself. While not necessary for 802.1x/MAB authentication, it does add additional information in RADIUS Accounting messages sent to ISE, and enriches the output of "show access-session interface..." command with some information, like Device Type and Device Name.
Global Device Sensor Configuration
device-sensor filter-list dhcp list DS_DHCP_LIST
option name host-name
option name requested-address
option name parameter-request-list
option name class-identifier
option name client-identifier
device-sensor filter-spec dhcp include list DS_DHCP_LIST
cdp run
device-sensor filter-list cdp list DS_CDP_LIST
tlv name device-name
tlv name address-type
tlv name capabilities-type
tlv name platform-type
tlv name version-type
device-sensor filter-spec cdp include list DS_CDP_LIST
lldp run
device-sensor filter-list lldp list DS_LLDP_LIST
tlv name system-name
tlv name system-description
tlv name system-capabilities
device-sensor filter-spec lldp include list DS_LLDP_LIST
device-sensor notify all-changes
access-session attributes filter-list list DS_SEND_LIST
cdp
lldp
dhcp
access-session accounting attributes filter-spec include list DS_SEND_LIST
access-session authentication attributes filter-spec include list DS_SEND_LIST
Global IBNS 2.0 Class Maps and Service Templates
service-template CRITICAL_DATA_ACCESS
! You can choose not to specify a VLAN here if you just want to use whatever VLAN is already configured on the ports.
vlan XXX
access-group ACL-OPEN
service-template CRITICAL_VOICE_ACCESS
voice vlan
access-group ACL-OPEN
class-map type control subscriber match-all AAA_SVR_DOWN_AUTHD_HOST
match result-type aaa-timeout
match authorization-status authorized
class-map type control subscriber match-all AAA_SVR_DOWN_UNAUTHD_HOST
match result-type aaa-timeout
match authorization-status unauthorized
class-map type control subscriber match-all DOT1X
match method dot1x
class-map type control subscriber match-all DOT1X_FAILED
match method dot1x
match result-type method dot1x authoritative
class-map type control subscriber match-all DOT1X_NO_RESP
match method dot1x
match result-type method dot1x agent-not-found
class-map type control subscriber match-all DOT1X_TIMEOUT
match method dot1x
match result-type method dot1x method-timeout
match result-type method-timeout
class-map type control subscriber match-all MAB
match method mab
class-map type control subscriber match-all MAB_FAILED
match method mab
match result-type method mab authoritative
class-map type control subscriber match-any IN_CRITICAL_AUTH
match activated-service-template CRITICAL_DATA_ACCESS
match activated-service-template CRITICAL_VOICE_ACCESS
class-map type control subscriber match-none NOT_IN_CRITICAL_AUTH
match activated-service-template CRITICAL_DATA_ACCESS
match activated-service-template CRITICAL_VOICE_ACCESS
class-map type control subscriber match-all AUTHC_SUCCESS-AUTHZ_FAIL
match authorization-status unauthorized
match result-type success
ip access-list extended ACL-OPEN
permit ip any any
Global IBNS 2.0 Policy Maps
policy-map type control subscriber DOT1X_MAB_POLICY
event session-started match-all
10 class always do-until-failure
10 authenticate using dot1x priority 10
event authentication-failure match-first
5 class DOT1X_FAILED do-until-failure
10 terminate dot1x
20 authenticate using mab priority 20
10 class AAA_SVR_DOWN_UNAUTHD_HOST do-until-failure
10 clear-authenticated-data-hosts-on-port
20 activate service-template CRITICAL_DATA_ACCESS
30 activate service-template CRITICAL_VOICE_ACCESS
40 authorize
50 pause reauthentication
20 class AAA_SVR_DOWN_AUTHD_HOST do-until-failure
10 pause reauthentication
20 authorize
30 class DOT1X_NO_RESP do-until-failure
10 terminate dot1x
20 authenticate using mab priority 20
40 class DOT1X_TIMEOUT do-until-failure
10 terminate dot1x
20 authenticate using mab priority 20
50 class MAB_FAILED do-until-failure
10 terminate mab
20 authentication-restart 60
60 class always do-until-failure
10 terminate dot1x
20 terminate mab
30 authentication-restart 60
event agent-found match-all
10 class always do-until-failure
10 terminate mab
20 authenticate using dot1x priority 10
event aaa-available match-all
10 class IN_CRITICAL_AUTH do-until-failure
10 clear-session
20 class NOT_IN_CRITICAL_AUTH do-until-failure
10 resume reauthentication
event inactivity-timeout match-all
10 class always do-until-failure
10 clear-session
event authentication-success match-all
10 class always do-until-failure
10 activate service-template DEFAULT_LINKSEC_POLICY_SHOULD_SECURE
event violation match-all
10 class always do-until-failure
10 restrict
event authorization-failure match-all
10 class AUTHC_SUCCESS-AUTHZ_FAIL do-until-failure
10 authentication-restart 60
Trunk Port Interface Configuration
interface Te1/1/1
switchport mode trunk
switchport nonegotiate
ip dhcp snooping trust
no access-session monitor
device-tracking attach-policy DISABLE-IP-TRACKING
Open Mode Access Port Template Configuration
Create a Template using the commands below to make it easy to switch between Open Mode and Closed Mode.
Open Mode is the default mode of switch ports, which is only visible due to the fact that the switch ports are missing the “access-session closed” command, which you can see below when comparing the two templates.
In Open Mode, the switch will ignore any “ACCESS-REJECT” responses sent from the RADIUS server and apply whichever DATA VLAN is already configured on the switch port.
However, Open Mode does not ignore specific Authorization results (like VLAN/dACL/SGT assignment) that are returned by the RADIUS server, so make sure to use a different Policy Set for switches running in Open Mode (also known as “Monitor Mode”) to keep your implementation organized. The Policy Set(s) for Open Mode should in general only contain simple “ACCESS-ACCEPT” results with a Reauthentication Timer, nothing fancier.
template WIRED_DOT1X_OPEN
dot1x pae authenticator
dot1x timeout tx-period 7
dot1x max-reauth-req 2
mab
subscriber aging inactivity-timer 60 probe
access-session control-direction in
access-session host-mode multi-auth
access-session port-control auto
authentication periodic
authentication timer reauthenticate server
service-policy type control subscriber DOT1X_MAB_POLICY
Change the "host-mode" parameter to fit your needs:
Select "multi-auth" to authenticate multiple DATA devices individually and one VOICE device.
Select "multi-domain" if you only want to authenticate one DATA device and one VOICE device.
Select "single-host" if you only want to authenticate one MAC address in total.
Select "multi-host" if you only want to authenticate the first MAC address and allow all other MAC addresses that appear after the first one (huge security risk!).
Closed Mode Access Port Template Configuration
Create a Template using the commands below to make it easy to switch between Open Mode and Closed Mode.
template WIRED_DOT1X_CLOSED
dot1x pae authenticator
dot1x timeout tx-period 7
dot1x max-reauth-req 2
mab
subscriber aging inactivity-timer 60 probe
access-session control-direction in
access-session host-mode multi-auth
access-session closed
access-session port-control auto
authentication periodic
authentication timer reauthenticate server
service-policy type control subscriber DOT1X_MAB_POLICY
Change the "host-mode" parameter to fit your needs:
Select "multi-auth" to authenticate multiple DATA devices individually and one VOICE device.
Select "multi-domain" if you only want to authenticate one DATA device and one VOICE device.
Select "single-host" if you only want to authenticate one MAC address in total.
Select "multi-host" if you only want to authenticate the first MAC address and allow all other MAC addresses that appear after the first one (huge security risk!).
General Access Port Interface Configuration
interface range Gigabit1/0/1 - 24
switchport mode access
switchport access vlan XXX
switchport voice vlan YYY
switchport nonegotiate
no switchport port-security
device-tracking attach-policy IP-TRACKING
ip dhcp snooping limit rate 20
no macro auto processing
storm-control broadcast level pps 100 80
storm-control action trap
spanning-tree portfast
spanning-tree bpduguard enable
spanning-tree guard root
load-interval 30
! Choose which mode to put the switch port in.
! Activate OPEN MODE using the configured template:
source template WIRED_DOT1X_OPEN
! Activate CLOSED MODE using the configured template:
source template WIRED_DOT1X_CLOSED
When you use Port Templates, use the command "show derived-config" to see the actual (total) configuration on an interface after the Template has been applied to it.
While you can put even more of the general interface configuration commands into a Template that I have done above, I have had some mixed results, such as some specific commands in the Port Template not being applied after a switch reload, which is probably a bug, so keep an eye out for that.
Verification and Show Commands
To verify your implementation, I suggest taking a look at the show commands found in this article: Cisco IBNS 2.0 - Work Faster with Aliases for Show Commands (IOS and IOS-XE).