Introduction
This article is the startup point of a complete RadSec (RADIUS over TLS/DTLS) configuration using a Cisco device (switch), Cisco ISE and using Microsoft’s Active Directory Certificate Services to issue the certificates needed, both using the manual approach and automated approach with the SCEP protocol.
Since this is somewhat of an advanced topic, this series of articles assume you already have an Active Directory with Certificate Services up and running. You are expected to already have some knowledge and be familiar with working with certificates (and PKI) and Cisco ISE, in general.
In this series of articles, the following hardware and software are being used.
Cisco Catalyst C9200L-48P-4X Switch running IOS-XE 17.3.5
Cisco ISE version 2.7
Microsoft Windows Server 2016
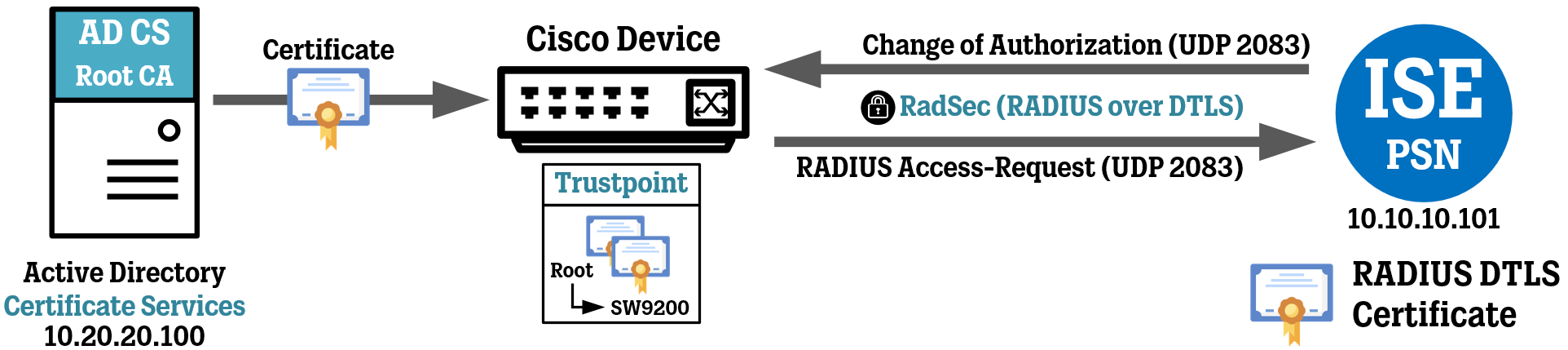
Why RadSec instead of regular RADIUS?
RadSec offers much greater security for communication between Network Devices (switches/routers/WLAN controllers etc.) and the RADIUS server they need to talk use to authenticate endpoint and users. Regular RADIUS uses a Shared Secret password for authentication between the Network Device and the RADIUS Server, and uses a weak MD5 hash function for security measures.
RadSec on the other hand uses certificates for mutual authentication between the Network Device and ISE, and also provides strong encryption using TLS or DTLS.
RadSec is especially important if you are connecting your on-prem Network Devices to a cloud hosted RADIUS server, since this traffic will be transported over the internet.
Other differences between RadSec and regular RADIUS
Regular RADIUS uses UDP ports 1812/1813 (new) or 1645/1646 (legacy) for authentication/authorization and accounting respectively, and for Change of Authorization (“CoA”), the UDP port 1700/3799 (ISE/non-ISE servers) are used.
In RadSec, port usage has been simplified somewhat and the only relevant port is port UDP or TCP 2083, depending on if you are using TLS (uses TCP) or DTLS (uses UDP). These ports are used for all aspects of the deployment (for authentication/authorization/accounting and Change of Authorization) and need to be open through firewalls in both directions between the Network Device and Cisco ISE.
Throughout this series, we will use RADIUS over DTLS for our RadSec implementation, since this is the only mode available for Cisco ISE.
Getting Started
With that little intro done, it is time to get started with the configuration.
Down below, you have links to all the articles of the series.
Cisco RadSec Part 1 - RADIUS over TLS/DTLS Overview <—— you are here!
Cisco RadSec Part 2 - RadSec Certificate Template using Microsoft AD Certificate Services
Cisco RadSec Part 3 - Cisco Device Manual Certificate Enrollment
Cisco RadSec Part 4 - Cisco Device SCEP Certificate Enrollment
Cisco RadSec Part 5 - Cisco ISE RadSec Configuration
Cisco RadSec Part 6 - Cisco Device RadSec Configuration
Cisco RadSec Part 7 - Testing, Troubleshooting and Show Commands
Next part: Cisco RadSec Part 2 - RadSec Certificate Template using Microsoft AD Certificate Services