Introduction
Cisco’s AnyConnect VPN client software is something probably most people in the IT business have run into more than a few times, and in my opinion, it is one of the most solid Remote Access VPN software I have ever used.
While the AnyConnect Suite has grown over the years to include a lot of different endpoint software, the VPN module is probably the most utilized one by far, as the solution as a whole is not too advanced to set up due to the vast amount of documentation available today, and deploying the AnyConnect VPN client software can be done either “on the go” to devices wishing to connect to the Remote Access VPN for the first time, or pre-deployed using pretty much any client management system.
However, a few years ago, I stumbled upon an open-source software called OpenConnect, that took a lot of inspiration from AnyConnect, more in than just name. This article is covering some of my testings with OpenConnect, and it has significant differences in terms of use with Cisco VPN-gateways, such as ASA and Firepower firewalls.
OpenConnect is a Remote Access VPN client software that is built to work with a variety of different VPN-gateways (other than Cisco), as this image from their website below shows.
And it is no surprise that OpenConnect exists because a lot of Remote Access VPN software is built using various open-source projects and protocols. For example, if you open the GUI of Cisco AnyConnect and click on the “Information icon” in the bottom left corner, you can see some traces of this in the credits given.
Now, let’s get on with the testing!
Download the OpenConnect GUI Client
While the several ways to run OpenConnect on your endpoint, regardless of it running Windows, Linux or macOS, for these tests I will be using the OpenConnect GUI Client that can be run on Windows computers.
The OpenConnect GUI Client is available at the links below.
https://openconnect.github.io/openconnect-gui/
https://gitlab.com/openconnect/openconnect-gui
The installation is very straightforward, run the .exe-file to install the software.
OpenConnect GUI and Configuration Steps
In terms of the end-user experience, the GUI is very similar to that of most VPN client software.
Clicking on the “cogwheel” on the right side of the window opens up a menu that lets you manage Configuration Profiles. You can create a new “simple” profile or a new “advanced” profile, and edit or delete an already existing profile.
NEW PROFILE (“Simple”)
A “simple” configuration profile lets you input the IP address or Hostname to your VPN gateway, and assign a “friendly name” to it. You can use this kind of profile when the VPN service you will connect to only requires you to provide login credentials and possibly some other 2FA/MFA-authentication within the same RADIUS-flow, like One-Time Passwords (“OTP”).
NEW PROFILE (“ADVANCED”)
One thing I appreciate with OpenConnect is that you can create somewhat more advanced configuration profiles involving digital certificates in some way, right in the OpenConnect GUI, without the need of an external configuration tool (like Cisco’s Profile Editor inside ASDM or the standalone Profile Editor).
Creating a new advanced profile leads to the window below, where there are plenty of settings to configure a more sophisticated configuration profile.
Login Test with User Credentials
Next up, are some examples of using OpenConnect to connect to. Acting as VPN gateways are firewalls of models ASA 5545X and FPR-2120 (running ASA-code).
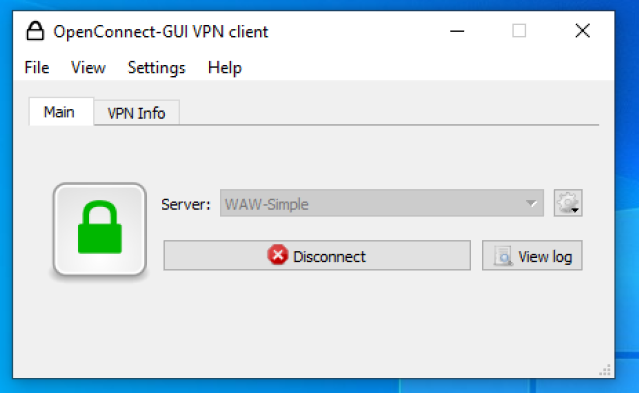
The first test is very simple, I will connect to a lab VPN gateway and log in using only a username and a password. I will call this profile “WAW-Simple”.
When I click on “Connect”, I am asked to enter a username followed by a password. The “lock” in the GUI is flashing yellow as the authentication is taking place.
When the authentication process is complete, the “lock” changes color to green, and the “Disconnect”-button can now be clicked to terminate the VPN connection.
Login Test with User Credentials + OTP-code
For the second test, I will once again create a simple profile (called “WAW-Simple-OTP”), but this time we will connect to a VPN gateway that is set up to send out an OTP-code via flash-SMS to my phone. After I enter my initial user credentials into OpenConnect, they are verified by the RADIUS-server in the backend and the flash-SMS is sent out, followed by me being challenged to enter the OTP-code as two-factor authentication:
And after entering the OTP-code, authentication is completed, and we are connected to the VPN gateway:
Logging and Troubleshooting
You can click on the “View log”-button to view a pretty decent log over your authentication and connection attempts, both successful and failed, which can be very useful for troubleshooting.
A lot of raw authentication data and RADIUS-information is displayed in the log shown in the image below, but also various parameters about your particular VPN-tunnel to the VPN-gateway, like routes added to your routing table and which encryption has been negotiated between OpenConnect and the VPN-gateway, can be viewed if you keep scrolling down in the log.
You can also find a snippet of this information by clicking on “VPN Info” in the main window of OpenConnect:
Notes of Interest
Automatically saves user credentials and selected Tunnel Group/Connection Profile, and uses them next time you wish to connect to a Profile that you have already been connected to before. The saving of user credentials has so far survived reboots of my test-PC as well, so the user credentials are not just saved “in memory” or similar. However, it is unsure where on my test-PC this information is saved, as I cannot find the answer to this in the documentation.
Supports selection of Tunnel Group/Connection Profiles, when more than one is offered by the VPN gateway.
No support for built-in SAML-based authentication.
No support for displaying post-login RADIUS-message, they can however be viewed in the log of the OpenConnect GUI Client after the authentication process has been completed.