Introduction
OpenSSL is often used to make changes to digital certificates, be it converting them from one type to another, combining multiple files into one, or splitting one bundle into multiple files.
This article contains some of the most commonly used commands I use every now and then.
If anything, this article is mostly a reminder post for myself so I don’t have to look them up elsewhere every time I need to make some changes to a certificate file.
Since I am mainly a Windows user, I will invoke OpenSSL 3.0 using “openssl.exe…” at the start of the command, which is run in the command prompt. If you are using the older OpenSSL 1.X versions or a Linux-based OS instead, you should replace “openssl.exe…” with just “openssl…” to run the commands.
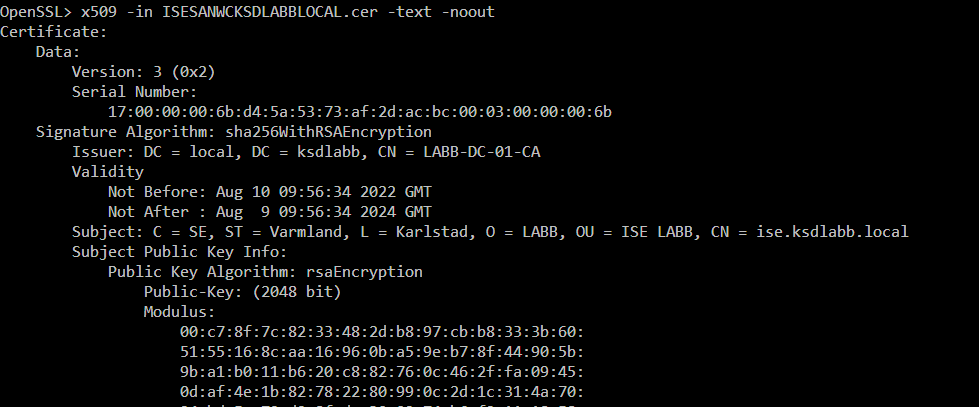
Display Contents of any Certificate file
openssl.exe x509 -in CERT.pem -text -noout
Display Contents of .PFX Certificate file (excluding Private Key)
openssl.exe pkcs12 -in CERT.pfx -info -nokeys
You will be asked to type in the Passphrase to display this information.
Display Contents of .PFX Certificate file (including Private Key)
openssl.exe pkcs12 -in CERT.pfx -info
You will be asked to type in the Passphrase to display this information.
Extract Certificate from .PFX file
openssl.exe pkcs12 -in CERT-and-KEY.pfx -clcerts -nokeys -out ONLY-CERT.crt
Extract Private Key from .PFX file
openssl.exe pkcs12 -in CERT-and-KEY.pfx -nocerts -out PRIV.key
Extract CA-chain from .PFX file
The result of this command depends on how the .PFX file was built and if the CA certificates were added individually or together (as one file) when the .PFX file was built. The order of how the CA certificates were added to the .PFX file can also influence the end result.
openssl.exe pkcs12 -in CERT-and-KEY.pfx -cacerts -nokeys -chain -out CA-CHAIN.cer
Combine Certificate and Private Key (without CA certificates) into .PFX file
Some applications require the .PFX file to contain the complete certificate chain to install the certificate in the application, which can be done using the command below.
openssl.exe pkcs12 -export -in ID-CERT.cer -inkey PRIV.key -out CERT-and-KEY.pfx
If the Private Key is encrypted, you will be asked for the Passphrase before the files are combined (and then set a new Passphrase for the PFX file).
Combine Certificate, Private Key and Full CA-chain into .PFX file
Some applications require the .PFX file to contain the complete certificate chain to install the certificate in the application, which can be done using the command below.
The CA-chain must be imported as a one file, you cannot add the CA certificates individually to the final .PFX file. Open up Notepad and create a file with the full CA chain by copypasting in the CA certificates into it. This CA chain file should be in .PEM-format and the order of the certificates should be:
intermediate (-----BEGIN CERTIFICATE-----)
root (-----BEGIN CERTIFICATE-----)
If your certificate consists of double intermediate certificate (for a total of 4 certificates for the complete chain including the identity certificate), create the CA chain accordingly:
intermediate2 (-----BEGIN CERTIFICATE-----)
intermediate1 (-----BEGIN CERTIFICATE-----)
root (-----BEGIN CERTIFICATE-----)
openssl.exe pkcs12 -export -in ID-CERT.cer -inkey PRIV.key -certfile CA-CHAIN.pem -out CERT-and-KEY.pfx
If the Private Key is encrypted, you will be asked for the Passphrase before the files are combined (and then set a new Passphrase for the .PFX file).
Combine Certificate, Private Key and Intermediate CA cert into .PFX file
Some applications require the .PFX file to contain the complete certificate chain to install the certificate in the application, which can be done using the command below.
openssl.exe pkcs12 -export -in ID-CERT.cer -inkey PRIV.key -certfile INTERMEDIATE-CA.cer -out CERT-and-KEY.pfx
If the Private Key is encrypted, you will be asked for the Passphrase before the files are combined (and then set a new Passphrase for the .PFX file).
Decrypt RSA/PKCS#1 (“unlock”) Private Key file
Use this command if your (encrypted) Private Key header starts with:
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
openssl.exe rsa -in ENCRYPTED.key -out PLAIN.key
(Followed by entering the current Passphrase)
Decrypt PKCS#8 (“unlock”) Private Key file
Use this command if your (encrypted) Private Key header starts with:
-----BEGIN ENCRYPTED PRIVATE KEY-----
openssl.exe pkcs8 -in ENCRYPTED.key -out PLAIN.key
(Followed by entering the current Passphrase)
Encrypt RSA/PKCS#1 (“lock”) Private Key file
Use this command if your (non-encrypted) Private Key header starts with:
-----BEGIN RSA PRIVATE KEY-----
openssl.exe rsa -in PLAIN.key -aes256 -out ENCRYPTED.key
(Followed by entering a new Passphrase)
Encrypt PKCS#8 (“lock”) Private Key file
Use this command if your (non-encrypted) Private Key header starts with:
-----BEGIN PRIVATE KEY-----
openssl.exe pkcs8 -topk8 -in PLAIN.key -out ENCRYPTED.key
(Followed by entering a new Passphrase)
Convert .PFX to .PEM
This command will use a .PFX file to create a .PEM file containing the ID certificate, the Root and/or Intermediate CA certificates, followed by the Private Key at the bottom of the file.
openssl.exe pkcs12 -in CERT-and-KEY.pfx -out CERT-and-KEY.pem -nodes
Convert .DER to .PEM
This command will use a DER (Binary encoded) certificate to create a .PEM (Base64 ASCII encoded) certificate:
openssl.exe x509 -inform der -in CERT.der -out CERT.pem
Convert .PEM (Base64 ASCII encoded) to .DER (Binary encoded)
This command will use a PEM (Base64 ASCII encoded) certificate to create a .DER (Binary encoded) certificate:
openssl.exe x509 -outform der -in CERT.pem -out CERT.der