In this article, we take a look at certificate requirements in Cisco ISE, specifically related to the different Extended Key Usages (“EKU”) available which you may need to communicate to your certificate management people before an ISE certificate is issued.
Introduction
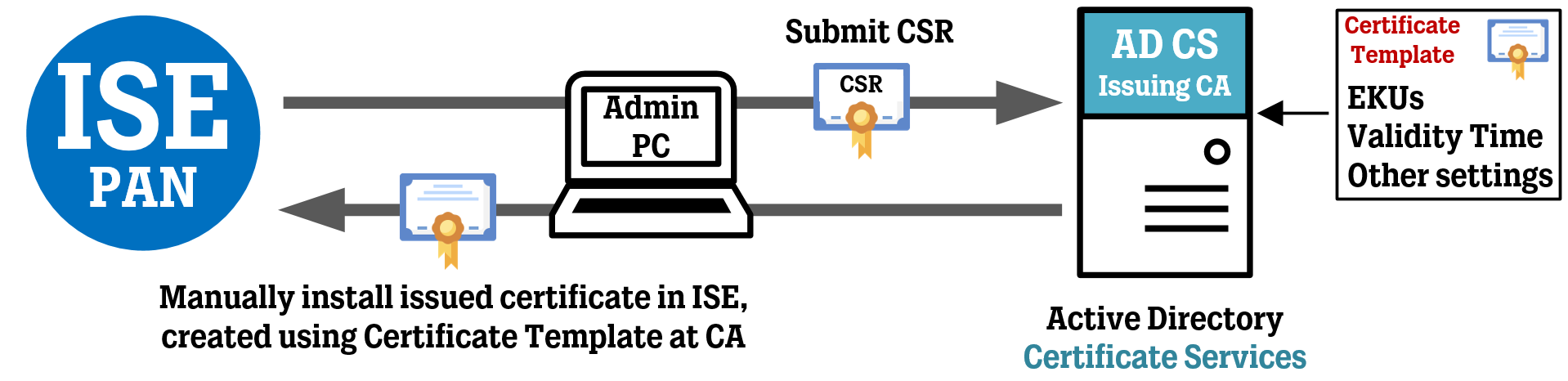
Setting up certificates properly in Cisco ISE is crucial for a successful deployment and getting it wrong can lead to big consequences. Certificates are usually created from Certificate Signing Requests (“CSR”) in which you, the ISE administrator, configure several hostnames or IP addresses that you want to be part of the finished certificate when the CSR is signed by a Certificate Authority (“CA”) and the actual certificate is created.
While this article is going to go through the Extended Key Usages needed for the different certificate uses in ISE, you can learn more about general certificate structures for ISE in an article I wrote several years ago, where I go through different choices in terms of working out the CommonName (“CN”), Subject Alternative Names (“SAN”) and wildcard attributes of different ISE certificates and deployment options.
You can find the article on this link: Certificates in ISE
In this article, however, we are going to go through the Extended Key Usage part.
What are Extended Key Usages?
Extended Key Usages are attributes on certificates that state what the certificate in question is supposed to be used for, or to put it more frankly, what is the certificate’s purpose.
Since certificates in ISE have different use cases, there are different requirements as to which of the Extended Key Usages need to be imprinted on the certificates when they are installed as System Certificates (meaning ISE can use these certificates as its identification).
The Extended Key Usages that are imprinted on a certificate are decided by the Certificate Authority that signs the CSR and issues the certificate. This is usually configured in the Certificate Template used by the Certificate Authority when the CSR is signed and the certificate is created.
For example, the most popular Certificate Authority service in the world is probably the one built into Microsoft’s Active Directory suite. This Certificate Authority comes loaded with a few different Certificate Templates by default, some of which can be used to issue ISE certificates right off the bat while some will need modification to fit the requirements.
Extended Key Usages for ISE certificates
Down below, I have put together a table of different certificates used in ISE and what kind of Extended Key Usages are required to be imprinted on the certificate used for that particular Usage (use case).
One of the references below states that for the RADIUS DTLS certificate, only Server Authentication is needed. However, from my own labbing experience, Client Authentication was also needed on this certificate to properly perform Change of Authorization (“CoA”) actions in some scenarios, which is why I have included it in my table above.
References
Configure EAP-TLS Authentication with ISE
Cisco Identity Services Engine Administrator Guide, Release 3.1