In this short article, we take a look at how to create a Redirection ACL on 9800 WLCs to use with Central Web Authentication for Cisco ISE guest access services and go through what each line of the ACL really does.
Introduction
This is not going to be a complete guide for how to set up guest access on ISE, the goal of this article is to simply go through the redirection ACL, which looks different from how it was done in the older AireOS WLCs, and the redirection ACL tends to look different is some places in Cisco’s documentation. Every time I have to set up a solution that requires a Redirection ACL I have had to look up how to do it because I can never remember, but maybe this article will change things.
The name of the Redirection ACL is what you should include in your ISE Authorization Profile’s Web Redication result, in the “ACL” field.
Configuration
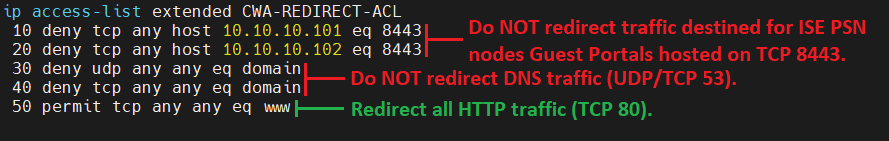
Replace the highlighted IP addresses below with the IP address(es) of your ISE deployments Polucy Service Nodes (PSNs).
ip access-list extended CWA-REDIRECT-ACL
10 deny tcp any host 10.10.10.101 eq 8443
20 deny tcp any host 10.10.10.102 eq 8443
30 deny udp any any eq domain
40 deny tcp any any eq domain
50 permit tcp any any eq www
There are some guides out there in which the last line of the ACL simply says “permit ip any any” which kind of works, but that also means that HTTPS (TCP 443) gets redirected, which will throw up a certificate error if HTTPS redirection is enabled (which you should avoid using, anyway).
If you would rather use the web UI to create the Redirection ACL, navigate to Configuration > Security > ACLs and click on the Add+ button. Configure the ACL according to the image below, except you have to switch out the IP addresses to match your deployment’s PSN nodes.