In this article, I share a template you can use for your wired ISE deployments to document which types of endpoints you have in your network, how they will authenticate to the network, and which type of network access they will be granted post-authentication.
Introduction
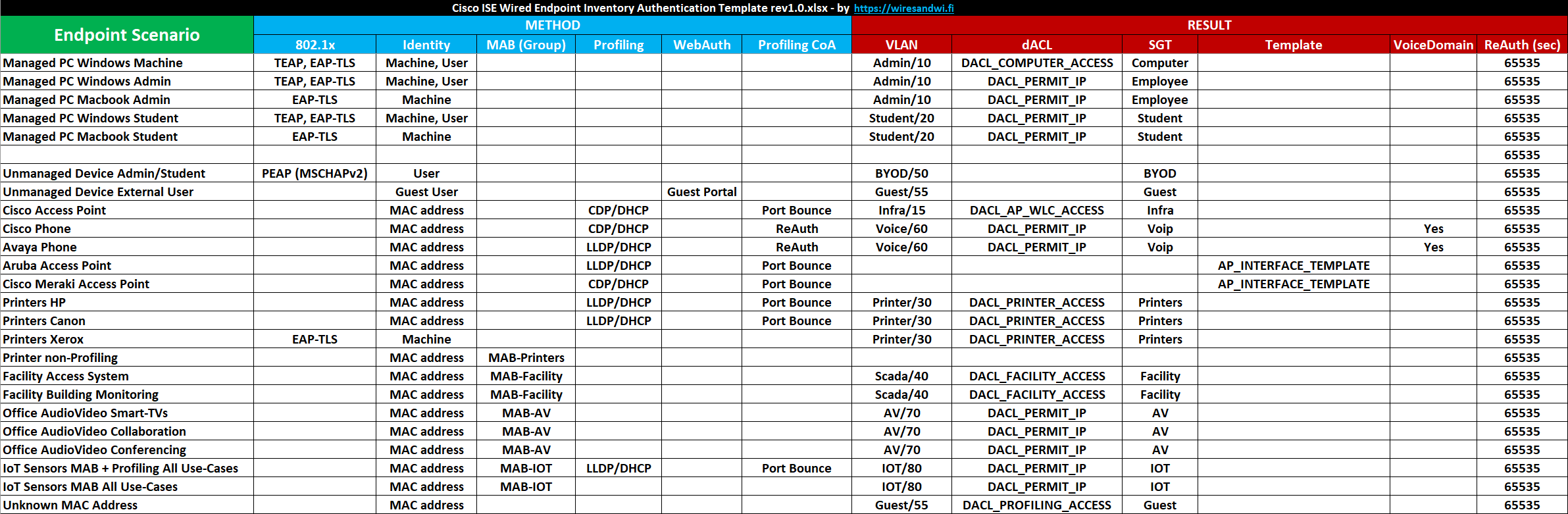
Both before and during your secure wired port implementation, it is useful to keep a record of all types of endpoints you have run into on your network and document which authentication method will be used to properly identify the endpoint and assign a suitable access to it. There are many ways to authenticate endpoints using different levels of authentication methods, some more secure than others and some methods can be combined to provide additional security.
Endpoint Template
This template could help you organize endpoints you are already aware of, in addition to endpoints, you might not have been aware of but discovered during your initial Open Mode deployment.
In the template, I have put together several examples of endpoints, authentication methods, and results to help you get going. Adjust the template to your specific organization’s environment and try to make a row for every type of endpoint you run into.
Download the template here (Excel):
Cisco ISE Wired Endpoint Inventory Authentication Template rev1.0.xlsx
Changelog
2023-02-01 - Revision 1.0 - first publication