In this article, we are going to take a look at different approaches to enable network administrators to use the “do” command on Cisco network devices where TACACS+ authentication is configured using Cisco ISE.
Introduction
Everyone who has worked with Cisco devices is used to be able to use classic Privileged EXEC (where the prompt looks like “Switch#”) commands like “show”, “ping” and “traceroute” at any time, even when the command prompt is in a different mode like Global Configuration mode, where the prompt looks like “Switch(config)#”.
By adding the “do” keyword in front of a Privileged EXEC command, for example, any “show” command, the command can be run directly in the Global Configuration mode, without the need to back out to Privileged EXEC (Switch#) before typing the command.
If you are using TACACS+ authentication on your network devices, getting the “do” command to work properly can be tough if you are utilizing per-command authorization, in which the TACACS+ authentication server (Cisco ISE) has to individually permit or deny every command executed by the network administrator. To solve this, we will look at different solutions in this article.
The following hardware and software were used in this article:
Cisco ISE version 3.1 patch 5 with Device Administration license active.
Cisco Catalyst C9200L-48P-4X Switch running IOS-XE 17.6.4
The Problem with “do” Commands and TACACS
While most of us are used to typing out “do” in front of commands like “show” commands to get them to run from any prompt, the correct (full) command is actually “do-exec”, and this is what will show up in your TACACS+ Live Logs on ISE should you try to run any “do…” command. Unfortunately, this means that if you add a show command as permitted in a TACACS Command Set, the “do” variant will NOT automatically be permitted too.
However, the logical processing of TACACS+ commands in TACACS Command Sets in Cisco ISE can be a little tricky to figure out sometimes, as the logic is slightly changed when you want to enable the “do” suffix of every command. From my testing, I have noticed that Cisco devices can have a hard time understanding which command the network administrator wants to use when they are putting “do” in front of it, as it sort of breaks the “autofill” feature, even though you can use the Tab key to autofill in many cases even when using “do” commands in IOS-XE devices.
The Solution
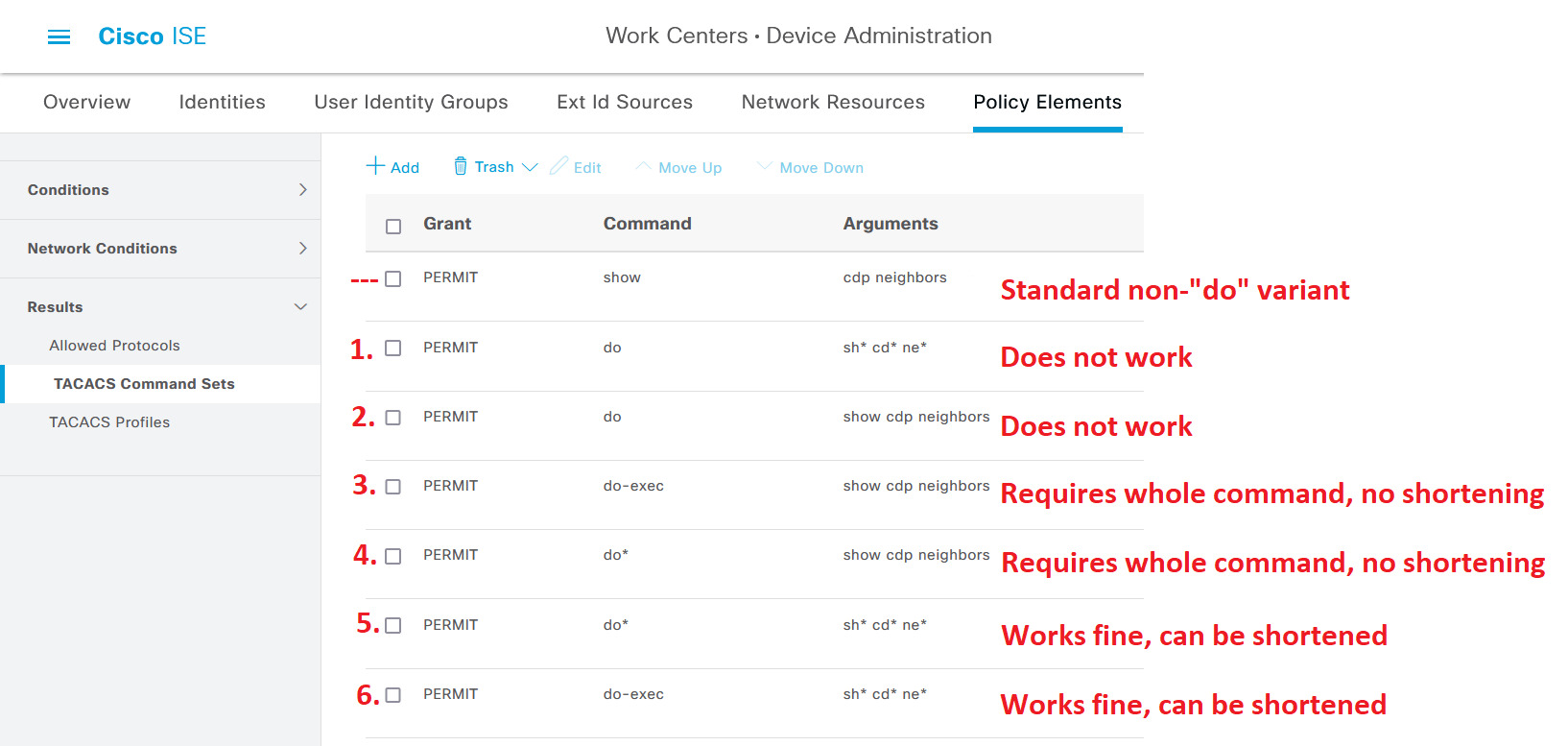
To further demonstrate the logic for “do” commands and Command Sets, we are going to look at some tests of running the command “show cdp neighbors” down below. The first row is the normal variant of the command, which is simply “show cdp neighbors”.
The next 6 rows (numbered from #1 up to #6) are different variants of adding “do” or “do-exec” in front of the original command, complete with an explanation of what the result and user experience would be trying to type the command using “do” in front of it.
Examples #1 and #2 do not work at all, no matter how you try to type them into the network device.
Examples #3 and #4 work to an extent, but they require that you type the whole command, like “do show cdp neighbors” to work, which is annoying, to say the least. You cannot leave out a single character in these examples, so shortening the command is out of the question.
Examples #5 and #6 work pretty well, you can type out either the full command or shorten it to a minimum, like “do sh cd ne”.
Final Notes
For a “do” command to work, the normal (non-”do”) variant of the command must also be permitted in the Command Set. This means that for every command you want to be able to run in both Privileged EXEC mode and Global Configuration mode, you will need two rows of configuration.
Using “do-exec” as the Command, followed by the command itself as an Argument “wildcarded” as much as possible (without enabling too wide of an available set of commands) would be my recommendation, as it is the clearest alternative. In the image above, this would be example #6.
If you have a TACACS Command Set for network administrators that gives full access to all commands by checking the “Permit any command that is not listed below” option, you will not have to worry about the “do” variant of commands, they will all work right out of the box.