If you are looking to deploy these features on older IOS switches (not the newer IOS-XE), please check out this article instead SOLID CONFIG: Cisco DHCP Snooping and IP Device Tracking for IOS Devices (non-SISF based).
This article is part of the “SOLID CONFIG” series, in which I cover some of the everyday configuration templates I have put together over the years to provide a solid configurational base for a specific feature, or use case.
Introduction
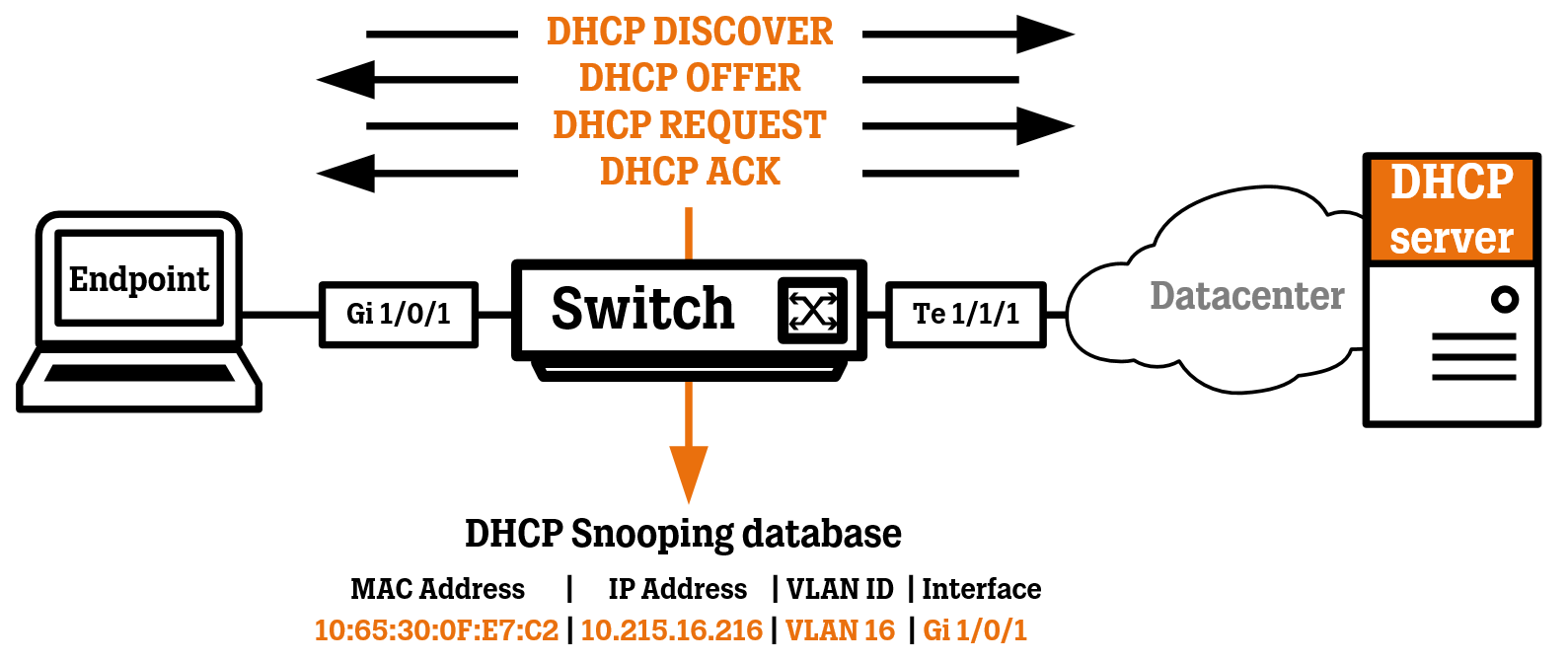
In this article, we take a look at the configuration steps for deploying DHCP Snooping and IP Device Tracking on access ports and trunk ports on Cisco IOS-XE switches using the new SISF-based configuration.
DHCP Snooping and IP Device Tracking provide some neat security and operational features, among them being a great way to find out the IP addresses of connected endpoints without having to resort to looking at ARP tables at the default gateways of a network and tracing MAC addresses.
The following configuration has been tested on:
Cisco Catalyst C9200L-48T-4X running version 16.12.5.
Cisco Catalyst C9200L-48P-4X running version 17.3.5.
About DHCP Snooping
DHCP Snooping provides a feature to protect against rogue DHCP servers in the network by only allowing ports configured as “trusted” to pass DHCP server messages. The switch will intercept (“snoop”) DHCP messages and take a peek inside of them to determine which IP address was assigned to a specific endpoint on a port. After an endpoint has gone through the whole process of DHCP leasing (Discover, Offer, Request, and Acknowledge), the result will be added to the DHCP Snooping database. Renewal of DHCP IP addresses (which are sent as DHCP-REQUESTS) will refresh the entry in the database. The switch will also clear the database of a certain DHCP IP address if it sees a “DHCP-RELEASE” packet being sent from the endpoint that the IP address in question belongs to.
About IP Device Tracking
IP Device Tracking uses the DHCP Snooping and Address Resolution Protocol (ARP) snooping features to build a database of IP-to-MAC binding present in the switch, making it easy to identify the IP address of every endpoint connected to the ports of the switch. ARP snooping works because the switch sees all the different ARP Probes/Requests/Replies being sent to and out from the connected endpoints and stores this information in the IP Device Tracking database.
The switch can then use its own “ARP Probes” to keep the information in the IP Device Tracking database up-to-date and accurate. If the endpoint doesn’t send or receive any ARP Probe/Request/Reply for a period of time, these IP Device Tracking “ARP Probes” are sent out in the port using the MAC address of the switch and IP address 0.0.0.0 as the source MAC and IP addresses. The endpoint, if still up and running, should respond to these ARP Probes, letting the switch know the endpoint is still active.
Both of these features are also very useful when deploying secured (authenticated) wired ports using a RADIUS server like Cisco ISE, where the connected host’s IP address needs to be inserted into Downloadable Access Control Lists (dACL). The Device Sensor uses both of these features to feed the RADIUS server with IP address information using RADIUS Accounting Update packets.
Now, time to get into the configuration steps.
Global DHCP Snooping and IP Device Tracking Configuration
This is the global configuration needed to get both IP DHCP Snooping and IP Device Tracking up and running. DHCP Snooping is enabled per VLAN, but since it is mainly an access layer feature, you should be fine by always enabling it for all VLANS (1-4094).
Compared to the “older” IOS software, most of the configuration for IP Device Tracking in IOS-XE is done in the global configuration as different Device Tracking Policies, which are then applied to the interfaces of the switch.
For trunk ports, the IP Device Tracking Policy configuration will disable all kinds of device tracking, since we do not want this feature running at all on trunk ports.
For access ports, the IP Device Tracking Policy configuration will limit the tracking to 2 MAC addresses, for example, one MAC address for a VOIP phone and one MAC address for a PC connected behind it.
ip dhcp snooping
no ip dhcp snooping information option
ip dhcp snooping vlan 1-4094
ip dhcp snooping database flash:dhcp-snooping-db.txt
device-tracking tracking auto-source
! Device Tracking Policy for Trunk Ports
device-tracking policy DISABLE-IP-TRACKING
tracking disable
trusted-port
device-role switch
! Device Tracking Policy for Access Ports
device-tracking policy IP-TRACKING
limit address-count 2
security-level glean
no protocol ndp
no protocol dhcp6
tracking enable reachable-lifetime 30
Trunk Port Interface Configuration
I would recommend configuring the trunk ports before the access ports. This configuration will configure the trunk ports as “trusted”, meaning DHCP server messages are allowed to be received on these ports. Since DHCP servers are usually located upstream in the data center or similar, make sure to configure this on all of your trunk ports. This configuration also applies a Device Tracking Policy with tracking disables, since it is a feature more suited for use on access ports, where the endpoints are connected.
interface Te1/1/1
switchport mode trunk
switchport nonegotiate
ip dhcp snooping trust
device-tracking attach-policy DISABLE-IP-TRACKING
Access Port Interface Configuration
This configuration will configure your access ports to rate-limit the number of DHCP packets that can be received on the port (per second). There is no need to configure the port as “untrusted” since that is the default state. IP Device Tracking will be configured according to the Device Tracking Policy we configured earlier in the global configuration.
interface range Gigabit0/1 - 24
switchport mode access
switchport access vlan XXX
switchport nonegotiate
device-tracking attach-policy IP-TRACKING
ip dhcp snooping limit rate 20
Show Commands
Use the command “show ip dhcp snooping binding” to see the IP addresses of all endpoints discovered using DHCP Snooping.
Use the command “show device-tracking database” to see the IP addresses of all endpoints discovered using either the DHCP Snooping or the IP Device Tracking’s ARP Snooping feature.
For example, the endpoint in the image below uses a static IP address, so it was discovered using ARP Snooping.