Introduction
In the past few years, QUIC has emerged as an alternative to TCP, trying to address the pros and cons of both old standards which are the TCP and UDP protocols to create a new protocol containing the best of both worlds.
We are not going to go through the complete history of QUIC (link), but long-story-short, this protocol was developed at Google to improve latency and bandwidth efficiency for users connecting to various Google services, like YouTube, when the Google Chrome web browser was used.
While unknown and invisible to most ordinary internet users today, QUIC has been somewhat successful in its goal, and has now been standardized and adopted both by several other services (like Facebook) and several other web browsers (like Firefox, Edge, and more).
From a firewall’s point of view, QUIC is problematic because it does not use the same encryptions methods used by most of today’s HTTPS/TLS/TCP connections, meaning the firewall cannot perform HTTPS Inspection on QUIC traffic.
Blocking QUIC Protocol
The simple solution to this problem is to block the QUIC-protocol from passing through your firewalls at all. All services/web browsers that have QUIC enabled will fall back to using normal TCP after a few milliseconds unless the service provider has goofed up on their side.
To properly block the QUIC protocol, we need to block both the UDP 80/443 ports (the “Services”) and the QUIC protocol (the “Application”).
Creating a custom Service Object
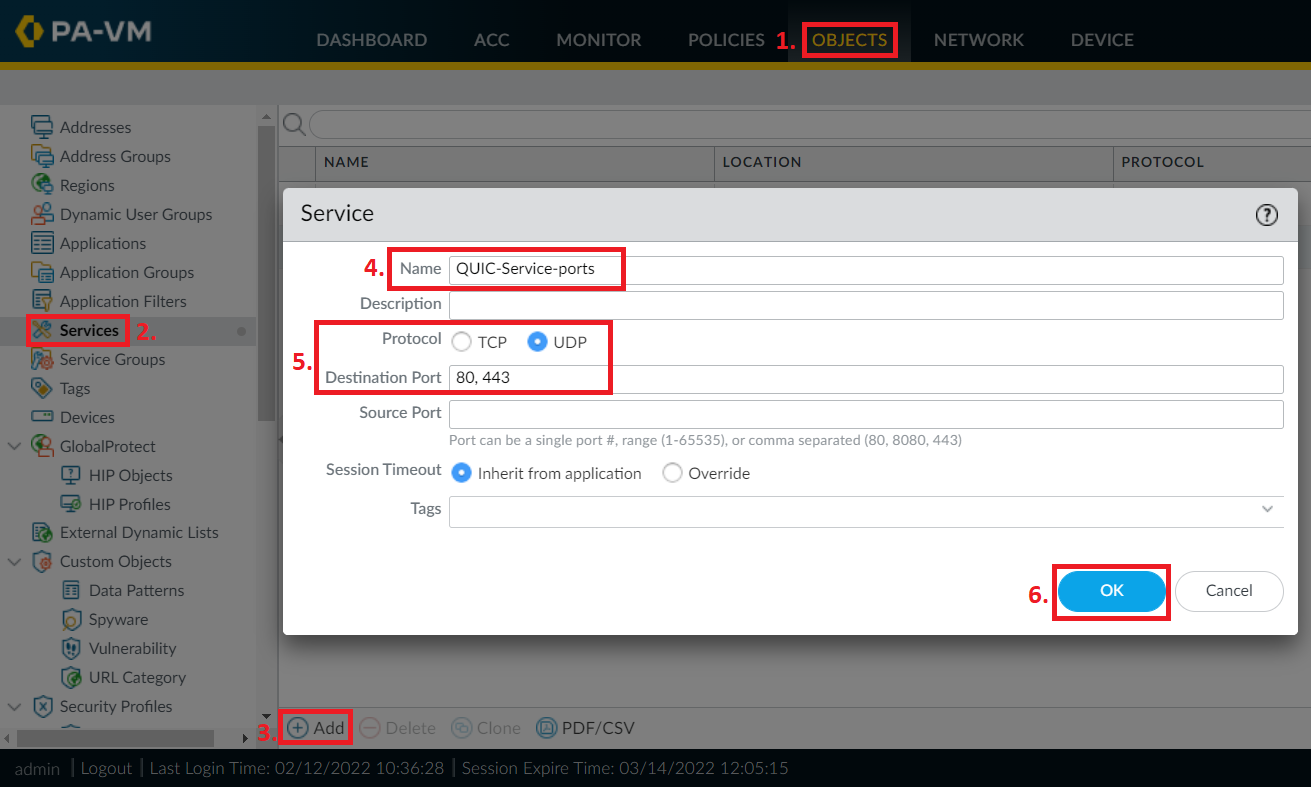
Create a custom Service object to represent UDP ports 80 and 443 by navigating to OBJECTS > Services and clicking on the +Add button at the bottom.
Give the Service a good name, select UDP as the Protocol and fill in the Destination Ports 80 and 443. You can leave the Source Port blank.
Create a new Policy Rule to Block Traffic
With the custom Service in place, head over to POLICIES > Security and create two new rules, one to block the custom Service ports and one to block the QUIC application.
Select your Zones/Sources/Destinations according to your needs, and create two rules similar to the rules in the image below. Make sure that these rules are set to the Deny action.
Commit your changes to activate the new policy rules.
Verification
Try to visit websites like Google, Youtube, or Facebook, and check in your live logs that UDP 80/443 and the QUIC protocol are being denied, while traffic to these services is still working correctly over TCP 80/443 instead, and is being HTTPS Inspected.