In addition to this article, I have now published a new article on the same subject which includes a more visual way of presenting the Windows network authentication process.
You can find the article here: Windows Network Authentication Sequence
Introduction
The goal of this post is to highlight some key differences between user and machine authentication and important facts you should know about.
Without further adu, let’s get into it.
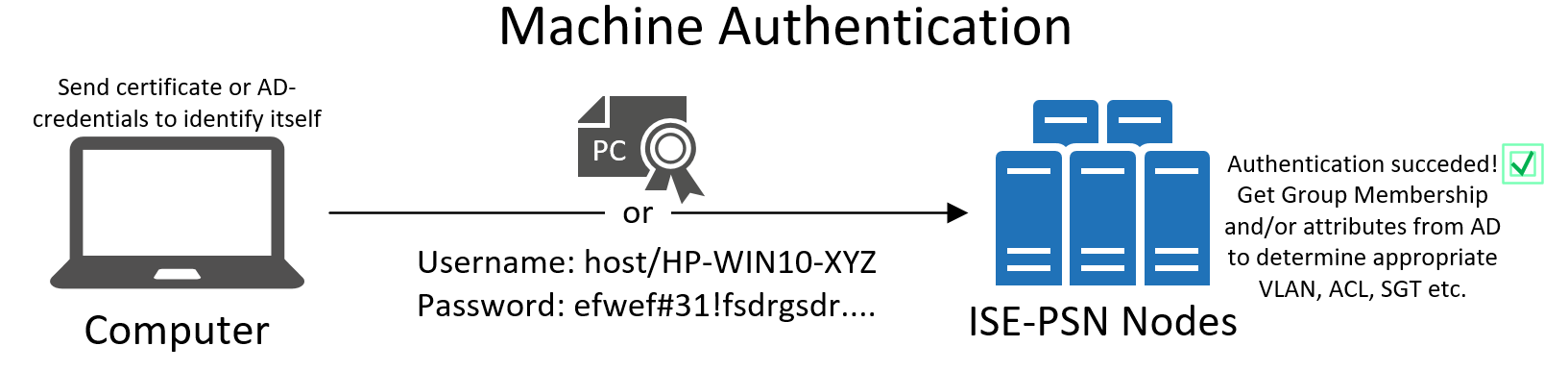
Machine Authentication (or Computer Authentication)
This type of authentication means the device itself will authenticate itself towards the network. Machine authentication is useful because it will prove that the device connecting to the network is a trusted, corporate device. In this day and age it is most likely to be a laptop connecting either to the wireless network or to the wired network.
The actual authentication can be performed using either certificates or credentials. During installation in an enterprise environment it is very common to populate the machines certificate store with a certificate that can be used to the machine to identify itself, not only to the network but to other services as well. Microsoft's Active Directory is probably the most common central management for computers today and it has the ability to run a Certificate Authority services in order to issue certificates to machines (and users).
In an Active Directory environment, every machine (computer) that joins the domain also has a set of credentials (think username/password) that can be used to log onto the domain. These credentials can also be used for network authentication. The machine credentials can be viewed if you dig deep into Windows but generally they are never shown to the user. Think of it as a username/password that only the machine knows about.
Now, depending on the requirements where network authentication is to be used, using ONLY machine authentication is a totally legit way to go. If you are implementing 802.1X on a network where every user has his or her own personal computer then machine authentication is a very good method to identify your users.
However, machine authentication falls short when you have users who share computers. Because only the machine is authenticated and not the user, you cannot for example assign different permissions (like VLANs) depending on who is using the computer. A bad example of this would be if a student on a school logs onto a teacher's computer. Because only the machine is authenticated, students and teachers would get access to the same network. In case this was a teacher's computer to begin with, that means the student now has access to the teachers' network... which is rarely good.
When does machine authentication take place if we are only running machine authentication (no user authentication)?
During bootup. When you boot up your computer it will perform the machine authentication even before you get to the Windows login screen.
When you log out. If the current user logs out then a new machine authentication will be triggered.
When you have Windows up and running and you turn off/on the WLAN NIC or simply disconnect/reconnect to the SSID.
When you have Windows up and running and you get back in range of an accesspoint broadcasting the SSID your network profile is configured for.
An important note is that the lock screen is not the same as logging out. The lock screen can be triggered either by the user manually or by an inactivity timer. The lock screen looks very similar to the login screen, especiallty since most lock screens today will require you to input your password to get back into Windows. The lock screen does not trigger a machine authentication. Putting the computer in Sleep/Hibernate mode doesn't either trigger machine authentication.
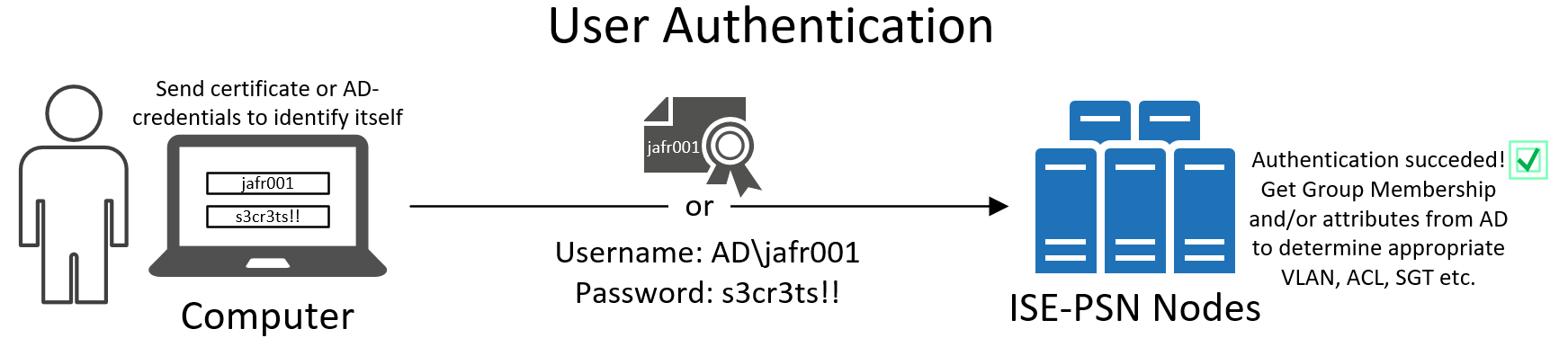
User Authentication
User authentication is the process when the actual user will identify themself to the network. Just like machine authentication, the authentication can be performed using either certificates or credentials. The user certificate is usually downloaded to the computer when the user logs into the computer for the first time.
Windows has a pretty convenient feature where the username/password used to log onto the computer will also be used to log onto the network. This is called Single Sign-On (SSO). This feature improves the user experience, otherwise the user would have to enter their username/password once more when they are greeted by the Windows desktop.
Using only user authentication has a big drawback and that is that the device connecting to the network could be any kind of device. Using certificate-based authentication could be considered somewhat secure since the certificate and its private key has to be pushed to the device when Windows is being installed or when the user logs in for the first time.
But what if you are using AD-credentials to connect to the network? Nothing would stop an employee from connecting their personal smartphone to the network by entering their AD-credentials into it. Personal devices should never be considered secure enough to connect to the corporate network and gain the same network access as corporate devices.
When does user authentication take place if we are only running user authentication (no machine authentication)?
When the user logs into Windows and certificates are used to authenticate the user.
When the user logs into Windows and AD-credentials are used to authenticate the user and you have Single Sign-On enabled.
If you don't have Single Sign-On enabled and the user logs into Windows, then proceed to manually log into the network when prompted to.
When you have Windows up and running and you turn off/on the WLAN NIC or simply disconnect/reconnect to the SSID.
When you have Windows up and running and you get back in range of an accesspoint broadcasting the SSID your network profile is configured for.
User AND Machine Authentication
This method is definitely considered the best because it ensures that the device connecting to the network is a corporate device and the person who is currently using the device can be assigned an approriate VLAN, ACL, SGT and so on depending on their position in the organization.
When does user and machine authentication take place when using both?
There is no single answer to this question because it varies depending on what kind of supplicant (the service/application that decides how you connect to the network) you are using and what type of EAP method is being used. Windows has it's own built-in network settings which can be used to configure user authentication, machine authentication or both but it has some drawbacks compared to using Cisco AnyConnect Network Access Module (NAM) to connect to the network. Simply put, AnyConnect has some features that are just smarter.
Windows built-in supplicant
If you are using Windows' built-in supplicant and you want to use both user and machine authentication then you have to choose either to use certificates or AD-credentials for BOTH authentications. You cannot mix them.
When using combined authentication, Machine Authentication takes place:
During bootup. When you boot up your computer it will perform the machine authentication even before you get to the Windows login screen.
When you log out. If the current user logs out then a new machine authentication will be triggered.
When using combined authentication, User Authentication takes place:
When the user logs into Windows and certificates are used to authenticate the user.
When the user logs into Windows and AD-credentials are used to authenticate the user and you have Single Sign-On enabled.
If you don't have Single Sign-On enabled and the user logs into Windows, then proceed to manually log into the network when prompted to.
When you have Windows up and running and you turn off/on the WLAN NIC or simply disconnect/reconnect to the SSID.
When you have Windows up and running and you get back in range of an accesspoint broadcasting the SSID your network profile is configured for.
The first authentication, the machine authentication, would result in the computer being placed in a temporary state with temporary VLAN, ACL, SGT until the user logs in, which will grant the user-specific access.
The authentications are completed as two seperate steps which comes at a cost when the machine authentication reaches it's session timeout and needs to be re-done. This means the user would have to reboot their computer or log out and then back in again to get network access. In an ISE deployment this session timeout can be configured up to a year, but it has a big drawback in distributed deployments because these sessions are not synced across all PSN nodes. You would also run in trouble when users are switching from a wireless connection to a wired and vice versa.
Cisco AnyConnect Network Access Module supplicant
If you are using Cisco AnyConnect Network Access Module to manage your network settings then you have the ability to mix certificate-based authentication and AD-credential-based authentication. You can set up AnyConnect NAM to work exactly like Windows built-in supplicant but there are even better ways of dealing with user and machine authentication.
You now have the ability to use an EAP method called EAP-FASTv2, which is developed by Cisco and so far only found in the AnyConnect program. EAP-FASTv2 solve all problems of the Windows supplicant by doing a combined user and machine authentication, meaning there will never be a problem where the machine's authentication has reached it's session timeout.
EAP-FASTv2 will be covered in a future post because it's really the best of the best when it comes to network access authentication. Like many of Cisco's own protocols, EAP-FASTv2 is being further development to become an open standard, which has been given the name TEAP (Tunneled EAP).